Modern computing systems are sprawling and complex, creating many opportunities for would-be intruders
to break-in and remain undetected.
Attackers can now dwell inside of networks for months or years before being noticed, as evidenced by numerous
high-profile data breaches in the news.
Our research seeks to empower system defenders by improving the ways in which we audit computers,
allowing them to understand and react to attacks before serious damage is inflicted.
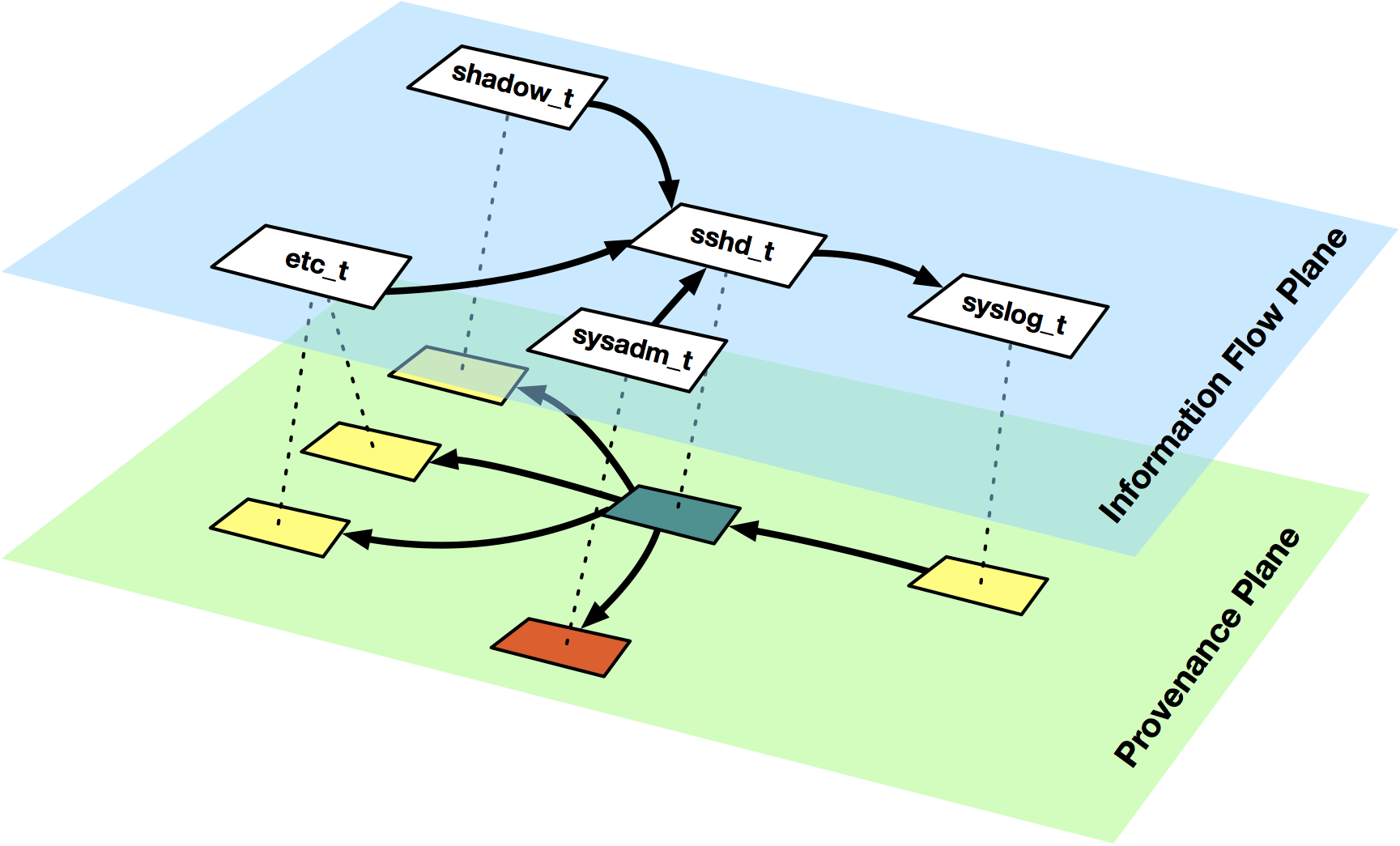
A key technique we leverage in this work isf data provenance, which iteratively parses low-level
events (e.g., Process A read File 1) into a causal dependency graph that describes the entire
history of system execution.
These graphs allow security analysts to identify the root causes of suspicious activities through causal analysis,
and can also be used to improve automated intrusion detection systems.
Recent Papers: